E-commerce has certainly been affected by last friday Dyn’s DNS attack.
And as a company that closely monitors the web performance of hundreds of e-commerce websites, running on several major CMS platforms, Quanta has had front row seats to the financial impact of such a massive DDoS attack.
But how and why such cyberattacks can affect the revenues of your e-commerce website?
What does DNS mean?
Before even talking about a DNS attack and its impact on e-commerce, it seems logical to talk about what is a DNS, and how it works.
Well, when a visitor wants to visit your website, he usually enters the address in his navigator, or clicks on a link from Google. The DNS, or Domain Name Servers, then works like a phone book for your website, providing the IP address of your website’s domain (commonly owned by your service provider) to the browser of your visitor.
For example. I am the proud owner of a Magento website, www.monsite.com, and my service provider is called KBS-System (or Oxalibe :P). When a user enters the address www.monsite.com in his navigator, his computer will start by requesting the corresponding IP address from the DNS server associated with the domain www.monsite.com.
This DNS server is usually not run by the service provider himself, because there are many specialized companies providing this type of service, like CloudFare, or Dyn, the company targeted by the October 18th attack. So in this example, the chain of request goes like this:
- Step 1: User’s navigator requests the IP address for www.monsite.com from Dyn’s DNS.
- Step 2: Dyn’s DNS responds with the IP address for www.monsite.com.
- Step 3: User’s navigator sends an HTTP request for www.monsite.com to the KBS-System’s server.
- Step 4: KBS-System’s server responds by providing the home page for www.monsite.com.
As you can see, it’s rather simple. It is a well-oiled communication funnel between a user’s laptop, a DNS, and a website’s server. Usually, the 2 first steps happen in only a fraction of a second.
The impact of a DDoS attack on e-commerce
But how a simple communication process like this could affect an e-commerce website?
Well, simply by being the subject of an attack. And in the case of last week Dyn’s DNS attack, a massive DDoS attack.
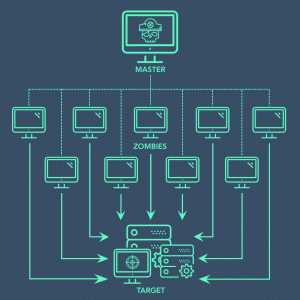
A Distributed Denial-of-Service attack is when infected machines are used to flood a designated target with superfluous requests in an attempt to render it slow or unavailable.
And in this case, the target of the Dyn’s DNS attack wasn’t service providers. None were targeted. It was the DNS server itself. And if you take a second look at the 4 steps of a DNS request that I explained above, you’ll understand what happened.
If the DNS is the subject of a massive DDoS attack, then it could become unavailable, or extremely slow, and thus, the attempt to reach a given website (in this case, your e-commerce platform) would stop at Step 1.
A request would be sent to the DNS by a user, but flooded by the attack, the DNS wouldn’t be able to respond. Thus leading to:
- no IP address,
- no connection to your website,
- no page displayed,
- and finally, no sale.
Shopify and the 2016 Dyn cyberattack
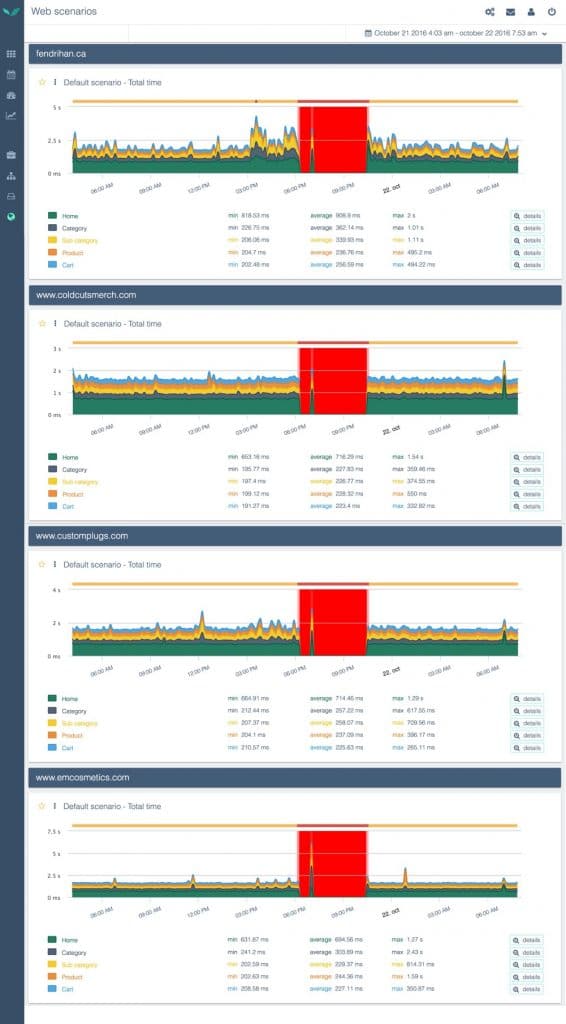
Quanta monitors the web performance of the sales funnel pages of more than 500 e-commerce websites. It represents more than 10 million pages each day.
And amongst these websites, there are those that run on the CMS Shopify.
Those particular e-commerce platforms were greatly impacted by last friday’s attack, simply because 40% of them used Dyn’s DNS servers. Those affected websites chose the basic DNS configuration offered by Shopify which contains a redirection towards the shopify.com domain, affected by the Dyn attack.
The other 60% chose to go with their own DNS servers instead of Shopify’s, and thus weren’t affected.
As we’ve explained before, the websites running with Shopify’s basic DNS configuration were affected because the probe couldn’t find their IP address. The users of these websites were faced with “Cannot resolve host” errors, meaning that the DNS request had failed.
It’s like we said in our study on “What is the Best E-Commerce Platform for Web Performance?”, highlighting the fact that Shopify is, to this day, the best CMS for e-commerce in terms of web performance. Shopify is an “all-included” CMS platform so if you choose to go with it, and its default server configuration, you run the risk of exposing your website to incidents affecting Shopify’s servers.
Several monitored Shopify-based e-commerce websites, crashing at the same time
But keep in mind that e-commerce websites are not helpless in front of such threats. There are some good practices that could help your e-commerce website to reduce, or even prevent, the impact of such attacks.
Good practices: How to protect e-businesses
In case of an international attack, like last friday’s, there is little you could do to completely prevent the impact of an attack on your website. But as I’ve said before, there are some good practices that you could implement easily.
- Choose, from the very start, 2 DNS providers: The idea is quite simple there. Don’t put all your eggs in the same basket. In the event of an attack, the probability is sleem that two different providers would be targeted. So, at least, with two of them, you’ll always have a backup. If you already set up your DNS provider, at least, be ready to an unaffected one, at any moment. And for that you just have to prepare beforehand a migration of your DNS from one provider to another. You don’t even need the authorization of your first DNS provider to do so. You can do it with your registrar (ex: NetNames, Gandi, …etc.).
- Choose DNS providers that takes security seriously and posses servers all around the globe: Exactly like for the adjonction of frontal servers for your website, the more servers a DNS provider has, the more he will be able to sustain the charge in case of an afflux of requests.
- Load external resources and scripts asynchronously: It is possible that in the event of an attack on a DNS provider, your website wouldn’t be affected. But the possibility remains for your website to crash or get awfully slow, if you didn’t take the precaution to load asynchronously external resources and scripts (like external images, JS, CSS, …etc.). In this case, incidents that might affect the servers you are trying to reach for these resources, could impact your website performances or even render it unavailable. Be sure not to make your website page load dependent of external resources.
- Bonus – Technical good practice: Define longer Time To Live (TTL) parameters on DNS records. That way it will be possible to keep them in cache, and still reach the website for a time, even if the DNS provider is under attack, and thus, unavailable.